PCI Compliance for Windows Legacy

This guide helps you set up Sumo Logic Collectors, and install the PCI Compliance for Windows Legacy application, so you can begin monitoring your usage and determine if you are meeting Compliance benchmarks.
Log Types
The PCI Compliance For Windows Legacy App uses Windows Security Event and System Event logs. It does not work with third-party logs.
Sample Log Message
instance of Win32_NTLogEvent
{
Category = 13571;
CategoryString = "MPSSVC Rule-Level Policy Change";
ComputerName = "aphrodite.sumolab.org";
EventCode = 4957;
EventIdentifier = 4957;
EventType = 5;
InsertionStrings = {"CoreNet-IPHTTPS-In", "Core Networking - IPHTTPS (TCP-In)", "Local Port"};
Logfile = "Security";
Message = "Windows Firewall did not apply the following rule:
Rule Information:
ID: CoreNet-IPHTTPS-In
Name: Core Networking - IPHTTPS (TCP-In)
Error Information:
Reason: Local Port resolved to an empty set.";
RecordNumber = 1441653878;
SourceName = "Microsoft-Windows-Security-Auditing";
TimeGenerated = "20130411232352.140400-000";
TimeWritten = "20130411232352.140400-000";
Type = "Audit Failure";
};
Sample Query
_sourceCategory=OS/Windows/Events "Policy Change"
| parse regex "CategoryString = \"(?<category>[^\"]+?)\";[\s\S]+?Logfile = \"Security\""
| count by category
| where category matches "*Policy Change*"
Collecting Logs
This section provides instructions for configuring log collection for the PCI Compliance for Windows Legacy App.
Configure a Collector and a Source
To configure a collector and source, do the following:
- Configure an Installed Windows collector through the user interface or from the command line.
- Configure either a local or remote Windows Event Log source. To configure a Windows Event Log source set the following:
- Event Format. Select **Collect using legacy format.
Collect using legacy format.** Events retain their default text format from Windows.
For more information on local or remote Windows Event Log Source configuration, refer to Local Windows Event Log Source and Remote Windows Event Log Source.
Make sure to set the Source Category when configuring the Windows Event Log source. For example: OS/Windows/Events.
This section provides instructions for configuring log collection for the PCI Compliance for Windows Legacy App.
Installing the PCI Compliance for Windows Legacy App
This section provides instructions for installing the PCI Compliance for Windows Legacy App, along with examples of each of the App dashboards. The PCI Compliance for Windows Legacy App offers pre-built dashboards and queries to help you track your Windows system, user accounts, login activity, and Windows updates.
Now that you have set up collection, install the Sumo Logic App for PCI Compliance for Windows Legacy App to use the pre-configured searches and dashboards that provide insight into your data.
To install the app:
Locate and install the app you need from the App Catalog. If you want to see a preview of the dashboards included with the app before installing, click Preview Dashboards.
- From the App Catalog, search for and select the app.
- Select the version of the service you're using and click Add to Library.
Version selection is applicable only to a few apps currently. For more information, see Installing the Apps from the Library.
- To install the app, complete the following fields.
- App Name. You can retain the existing name, or enter a name of your choice for the app.
- Data Source. Select either of these options for the data source.
- Choose Source Category, and select a source category from the list.
- Choose Enter a Custom Data Filter, and enter a custom source category beginning with an underscore. Example: (
_sourceCategory=MyCategory).
- Advanced. Select the Location in Library (the default is the Personal folder in the library), or click New Folder to add a new folder.
- Click Add to Library.
Once an app is installed, it will appear in your Personal folder, or other folder that you specified. From here, you can share it with your organization.
Panels will start to fill automatically. It's important to note that each panel slowly fills with data matching the time range query and received since the panel was created. Results won't immediately be available, but with a bit of time, you'll see full graphs and maps.
Viewing the Windows Legacy PCI Compliance Dashboards
Windows - PCI Req 02, 08, 10 - Account, User, System Monitoring
Track your user accounts and recent system changes.
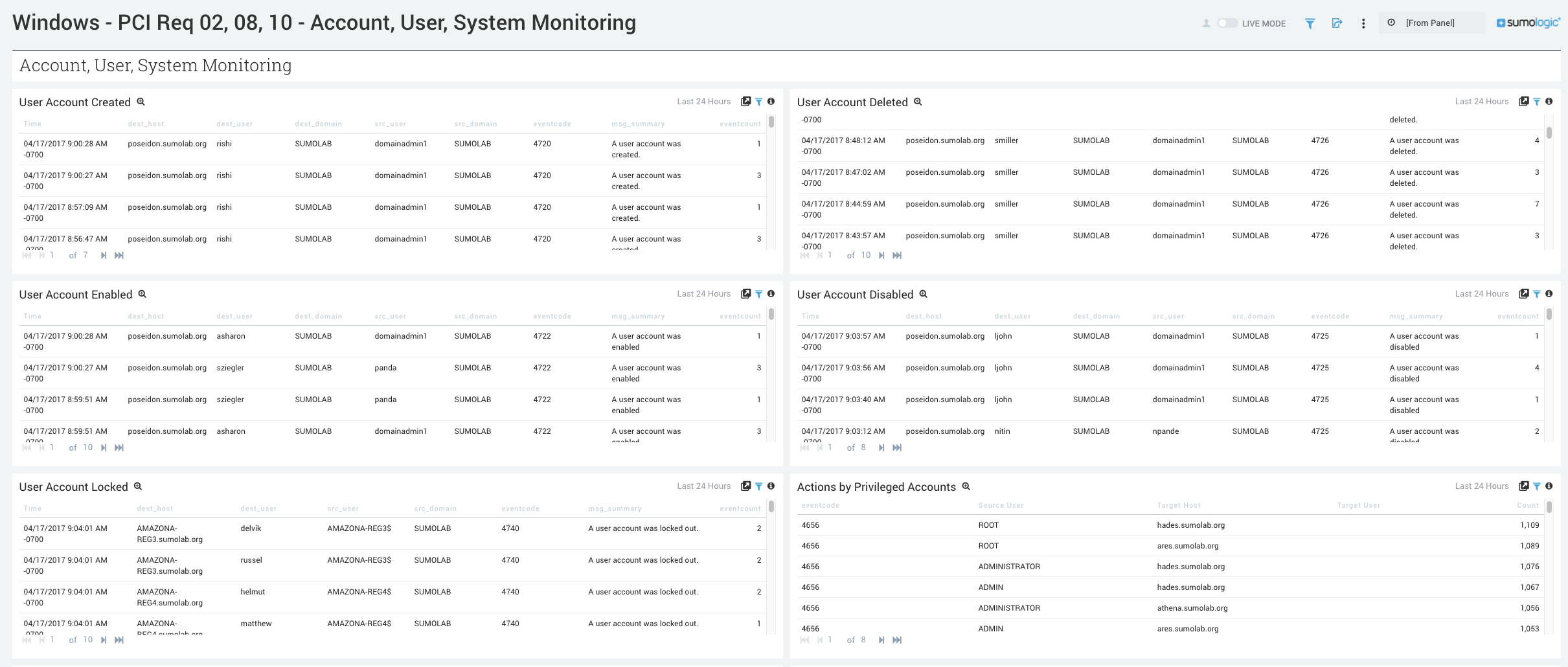
- User Account Created. Aggregation table of the number of user accounts created in the last 24 hours.
- User Account Deleted. Aggregation table of the number of user accounts deleted in the last 24 hours.
- User Account Enabled. Aggregation table of the number of user accounts enabled in the last 24 hours.
- User Account Disabled. Aggregation table of the number of user accounts disabled in the last 24 hours.
- User Account Locked. Aggregation table of the number of user accounts locked in the last 24 hours.
- Actions by Privileged Accounts. Aggregation table of the number of actions taken by privileged accounts over the last 24 hours.
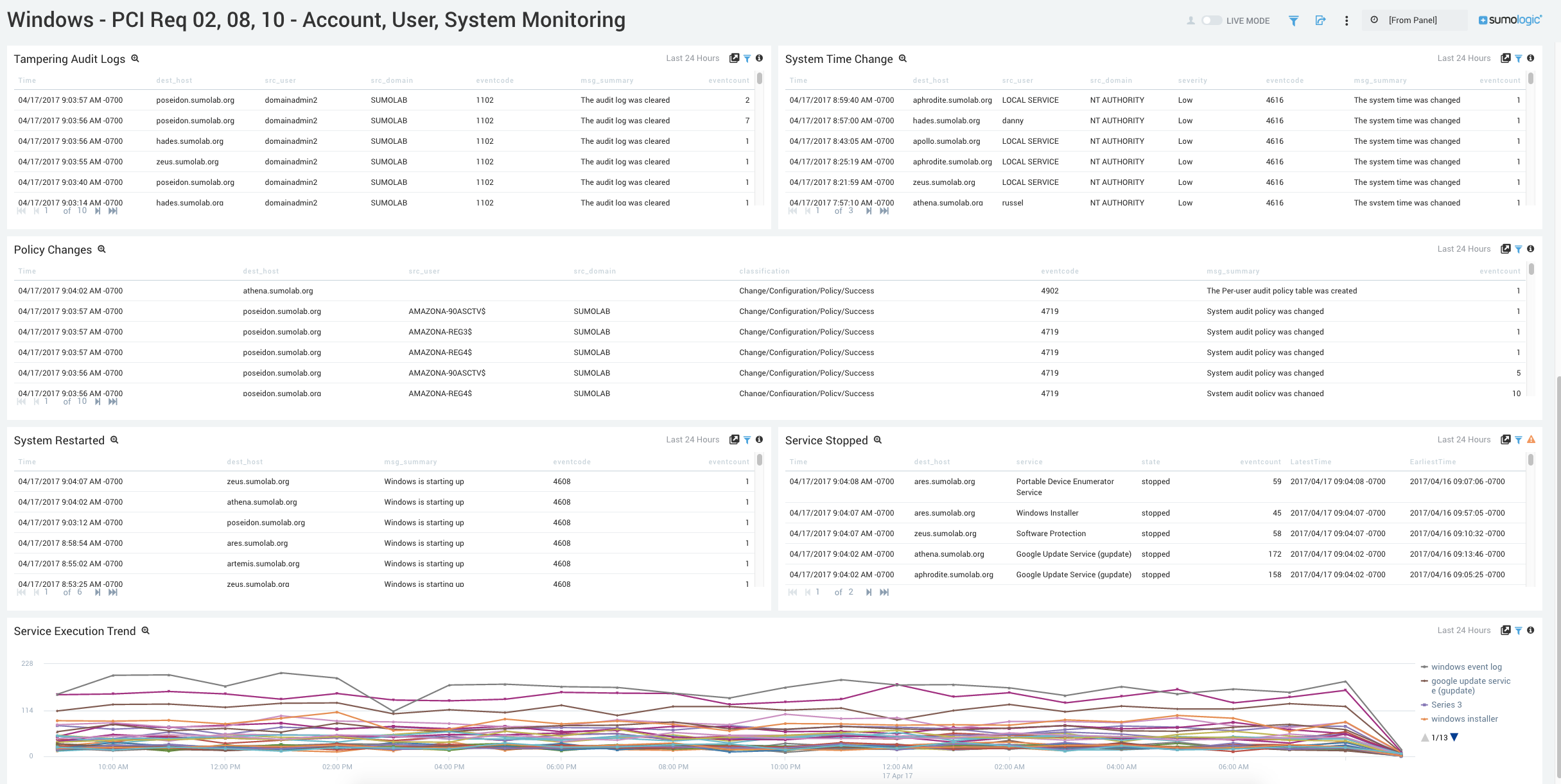
- Tampering Audit Logs. Aggregation table of the number of destination hosts whose logs were modified or cleared in the last 24 hours.
- System Time Change. Aggregation table of the number of services with a change to their system time over the last 24 hours.
- Policy Changes. Aggregation table of the number of services with policy changes over the last 24 hours.
- System Restarted. Aggregation table of the number of services started over the last 24 hours.
- Service Stopped. Aggregation table of the number of services stopped over the last 24 hours.
- Service Execution Trend. Trend of the different services being executed over time.
Windows - PCI Req 02, 10 - Login Activity
Track login successes and failures.
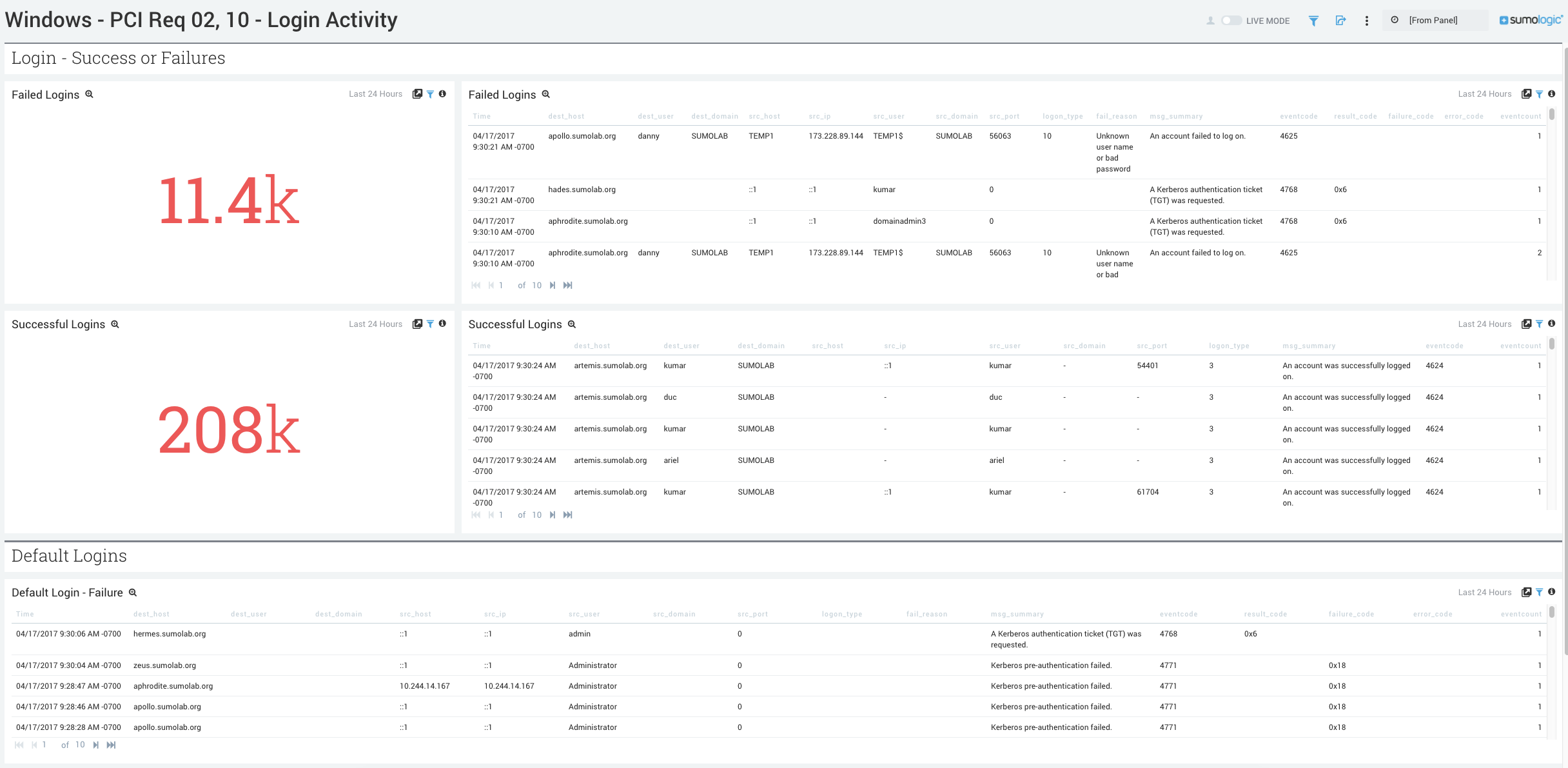
- Failed Logins. Count of failed logins over the last 24 hours.
- Failed Logins. Aggregation table of the date,
- Successful logins. Total number of successful logins over the last 24 hours. Compare to Failed Logins to determine if the number of failed logins to successful logins is consistent with normal behavior or indicative of an attack.
- Successful logins. Aggregation table of successful logins, including date, time, event code, error code, and count.
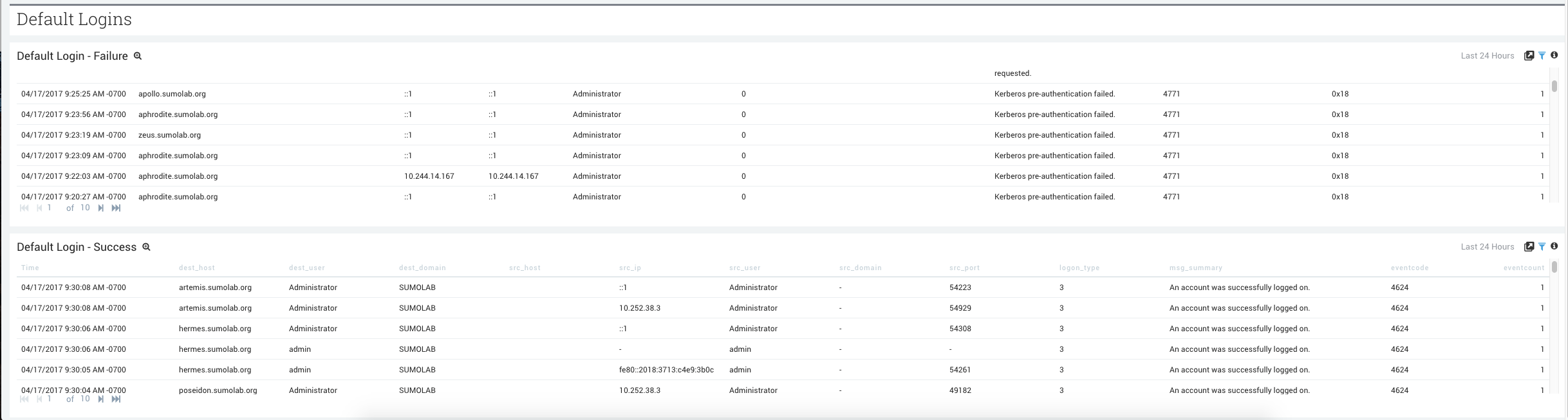
- Default Login-Failure. Aggregation table of failed default logins.
- Default Login-Success. Aggregation table of successful default logins.
Windows - PCI Req 08 - Other User Activity
Track user activities such as password changes, password resets, excessive failed access attempts, unlocked accounts, and disabled accounts.
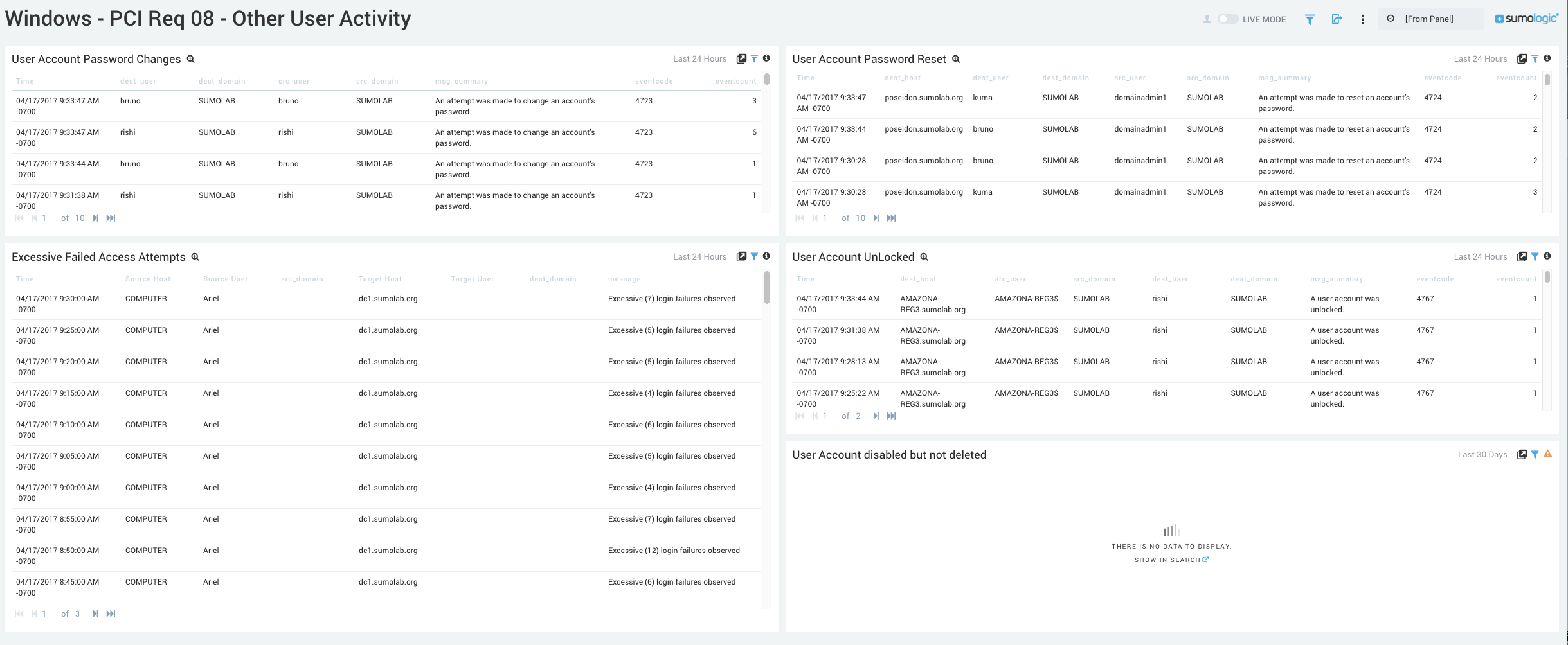
- User Account Password Changes. Displays an aggregation table of the times passwords were changed, the destination host, destination user, source host, and source user, source domain, error message, error code, and the number of events that occurred.
- User Account Password Reset. Displays an aggregation table of the times passwords were reset, the destination host, destination user, source host, and source user, source domain, error message, error code, and the number of events that occurred.
- Excessive Failed Access Attempts. Displays an aggregation table of the excessive failed access attempts, the destination host, destination user, source host, and source user, source domain, error message, error code, and the number of events that occurred.
- User Account Unlocked. Displays an aggregation table of the times a user account was unlocked the destination host, destination user, source host, and source user, source domain, error message, error code, and the number of events that occurred.
- User Account Disabled but not deleted. Displays an aggregation table of the times a user account was unlocked, the destination host, destination user, source host, and source user, source domain, error message, error code, and the number of events that occurred.
Windows - PCI Req 06 - Windows Updates Activity
Track your Windows Update activities.
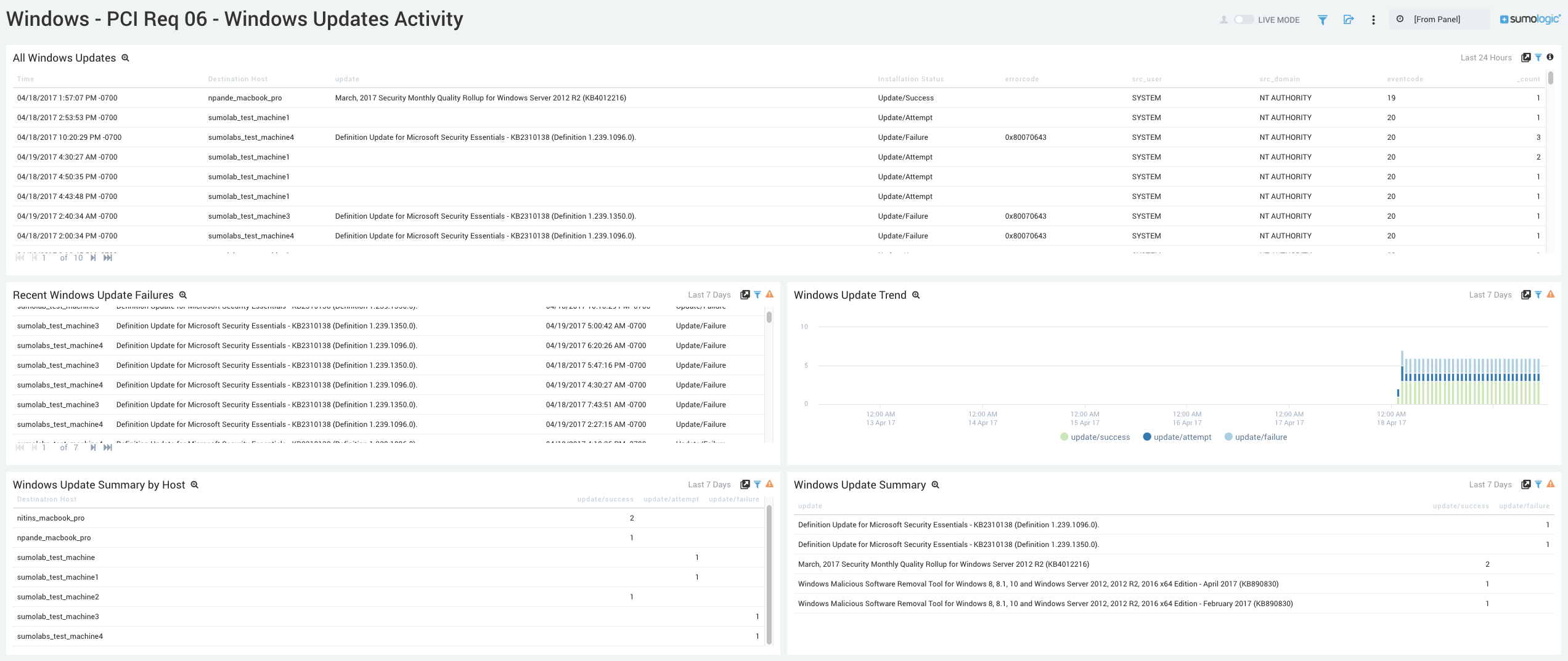
- All Windows Updates. Aggregation table displaying all updated hosts in the past 24 hours, success/failure of that update, and any relevant error codes.
- Recent Windows Update Failures. Aggregation table displaying all update failures in the last 7 days, update that failed, time of failure, and current status.
- Windows Update Trend. Bar chart that displays 7-day trend of updates success and failure time sliced by hour.
- Windows Update Summary by Host. Aggregation table of the hosts and a count of that host’s update success or failure for the past 7 days.
- Windows Update Summary. Aggregation table of the latest Windows updates for the last 7 days and a count of their successes and failures