Archive of July 2022 Cloud SIEM Release Notes.
July 28, 2022 - Application Update
Read-Only User Capabilities for CSE
New user capabilities (permissions) have been created enabling read-only access to content and configuration features in CSE.
These can be used when defining roles in the Sumo Logic platform (at Administration > Users and Roles > Roles).
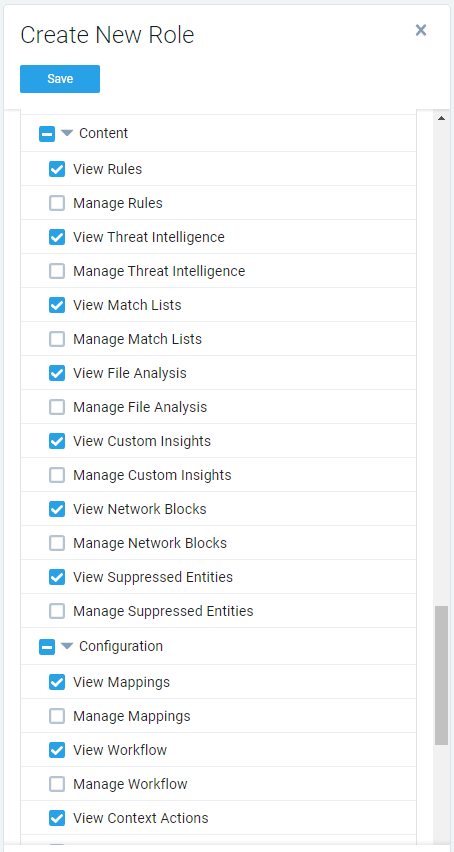
(For those with CSE instances in the jask.ai domain, these capabilities are accessed via the Configuration > Roles page in CSE.)
Users with these capabilities (without the corresponding Manage capabilities) will be able to view the corresponding pages but will not be able to make changes on those pages. (Previously, users without the Manage capabilities could not see the corresponding pages.)
These permissions also apply to CSE APIs, so View (only) capabilities can now be assigned if desired.
Minor Changes and Enhancements
- [Updated] When Threat Intelligence polling fails, the corresponding event will now include more information about the specific error that occurred.
- [Updated] The API endpoints that return information about Signals (
GET /signals, GET /signals/<id>, and GET /signals/all) now include the summary field (previously only accessible via the UI). - [New] The Sumo Logic audit logs will now include events when a user adds or removes a Signal to/from an Insight, and when a user adds a comment to an Insight.
Resolved Issues
- The
GET /rules and GET /rules/<id> API endpoints did not require role capabilities for access; they now require either View Rules or Manage Rules. - Favorite Fields were not always being displayed on Signals generated by Threshold Rules.
July 14, 2022 - Application Update
Minor Changes and Enhancements
- [Updated] The text size has been adjusted in some areas on the Rules details page to improve readability.
Resolved Issues
- In some instances, after uploading Network Blocks via .csv file, they would fail to appear in the UI.
Announcement Update
- The new Signal Index (recently announced) has been delayed, and will be available starting next week. As a result, the deprecation of the old Signal Forwarding feature will be delayed until September 22, 2022.
July 21 - Application Update
Entity Groups
There are a number of ways that the use of Entity attributes - tags, criticality and suppression - provide value to users of Cloud SIEM Enterprise: Investigations can be completed faster with more context, Insights can be better prioritized with the appropriate severity, and false positive signals from test instances can be prevented, for example. However, setting those attributes has been a manual process and keeping them in sync as new Entities are defined is difficult.
That's why we are pleased to announce a new feature called Entity Groups. By defining Entity Groups, attributes can be automatically applied (or removed) based on Entity value (name), IP address, or Inventory group membership. For example, all high-risk laptops will receive higher criticality -- even if such a laptop is added to your environment months later.
Entities can even be members of more than one Entity Group, so a high-risk laptop in the Austin office could both get a tag identifying its location and receive the higher criticality. And if you later reassigned it so that it was no longer in a high-risk group, the criticality would be automatically removed.
To create an Entity Group, a new configuration menu item has been added:
On the Entity Groups page, click the Create button:
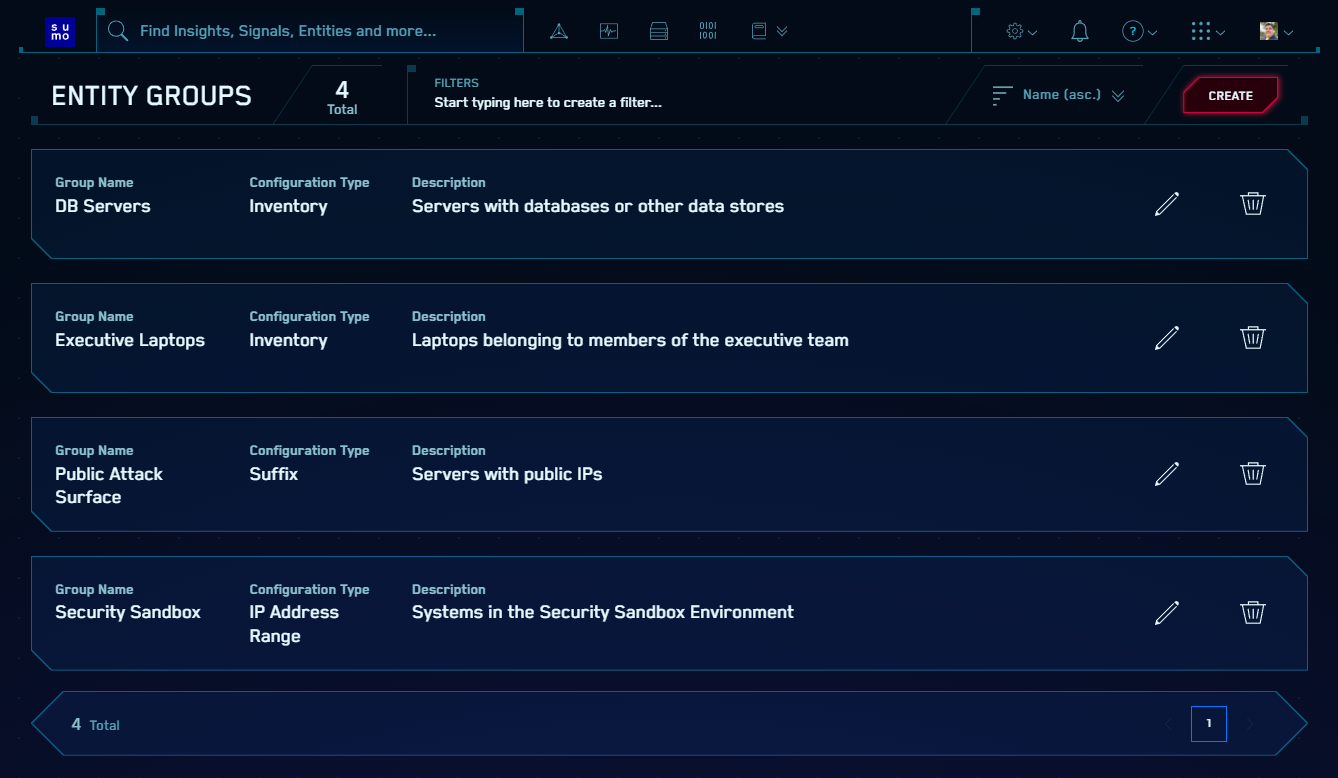
This will open the detail dialog:
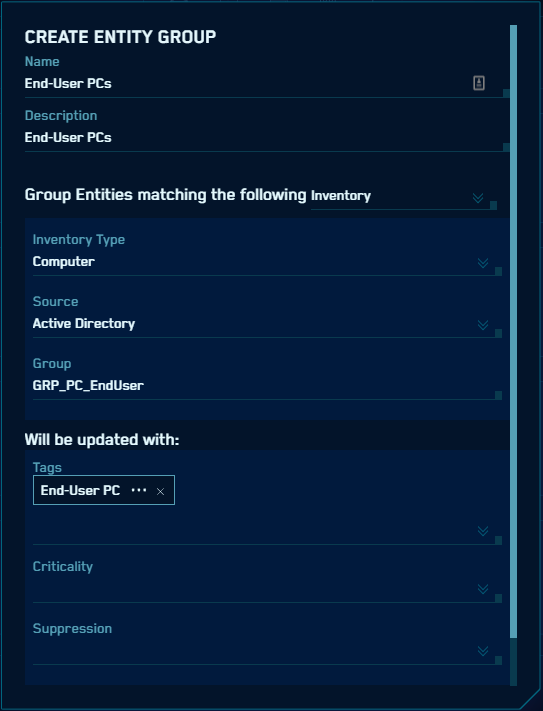
Here you can decide what attribute Group membership should be based on:
- Group membership in your Inventory system (such as Active Directory)
- Entity value (name) - prefix or suffix (such as "aus-" or "-public")
- IP address range (for IP Address entities) defined using the CIDR format
Entity Groups also support sensor zones.
Then you can define what attribute(s) should be applied to member Entities - tags, criticality and/or suppression.
This release also includes API and Terraform support for Entity Groups.
More information about this exciting new feature and how to use it is in the documentation at Using Entity Groups.
Signal Index
Starting today, Signals generated by Cloud SIEM Enterprise will be automatically saved in a new secsignal index. This special partition is similar to the existing sec_record* indices in that, unlike data retained using the older Signal Forwarding feature, it will be saved in proper JSON supporting keyword search and nested attributes.
The new index is automatically generated and retained for a period of 2 years at no additional cost for all CSE customers.
As a result, the optional Signal Forwarding feature will be deprecated on September 22, 2022. Existing data will not be deleted but new Signals generated after that date will no longer be forwarded and the option will no longer be available in CSE.
Customers leveraging Signal Forwarding data to generate dashboards (or for other use cases) will need to modify those applications to use the new sec_signal index before September 22.
Note that because the new index is a special partition, a single query cannot be used to search both the sec_signal index and older forwarded Signal data simultaneously.
More information about using the special security indices is in the documentation at Searching for CSE Data in Sumo Logic.
Minor Changes and Enhancements
- [Updated] The page used to configure the detection window and Insight threshold has moved. Where previously it was accessed from a button on the Custom Insights list page, it is now accessed via a new Workflow > Detection
option in the Configuration menu:
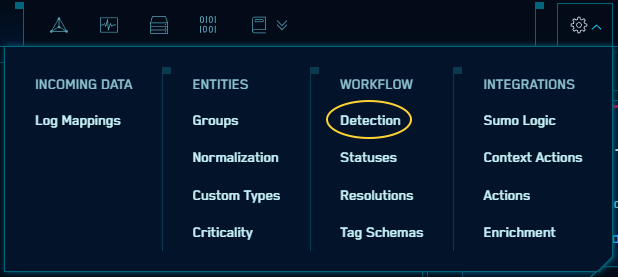
Note the URL has also changed as a result; please update any bookmarks.
Resolved Issues
When navigating to a CSE page (with sumologic.com in the domain name), if the user had to login/authenticate first, they were not auto-forwarded to the appropriate CSE page after doing so (but instead was taken to the Continuous Intelligence Platform home page). This has now been resolved and users will be auto-forwarded correctly.
July 21, 2021 - Content Release
Rules
- [Updated] MATCH-S00587 Empire PowerShell Launch Parameters
- [Updated] MATCH-S00161 Malicious PowerShell Get Commands
- [Updated] MATCH-S00190 Malicious PowerShell Invoke Commands
- [Updated] MATCH-S00191 Suspicious PowerShell Keywords
Log Mappers
Parsers
- [New] /Parsers/System/OSSEC/OSSEC JSON
- [Updated] /Parsers/System/Fortinet/Fortigate/Fortigate-Syslog
- [Updated] /Parsers/System/Kubernetes/Kubernetes
- [Updated] /Parsers/System/Palo Alto/PAN Firewall CSV
July 14, 2022 - Application Update
Minor Changes and Enhancements
- [Updated] The text size has been adjusted in some areas on the Rules details page to improve readability.
Resolved Issues
- In some instances, after uploading Network Blocks via .csv file, they would fail to appear in the UI.
Announcement Update
The new Signal Index (previously announced) has been delayed, and will be available starting next week. As a result, the deprecation of the old Signal Forwarding feature will be delayed until September 22, 2022.
July 14 - Content Release
Log Mappers
- [New] Carbon Black Cloud Alert - Tuned Activity
- [Updated] Cisco ASA 106001 JSON
- [Updated] Cisco ASA 106002 JSON
- [Updated] Cisco ASA 106006 JSON
- [Updated] Cisco ASA 106007 JSON
- [Updated] Cisco ASA 106010 JSON
- [Updated] Cisco ASA 106012 JSON
- [Updated] Cisco ASA 106014 JSON
- [Updated] Cisco ASA 106015 JSON
- [Updated] Cisco ASA 106021 JSON
- [Updated] Cisco ASA 106027 JSON
- [Updated] Cisco ASA 106100 JSON
- [Updated] Cisco ASA 106102-3 JSON
- [Updated] Cisco ASA 109005-8 JSON
- [Updated] Cisco ASA 110002 JSON
- [Updated] Cisco ASA 113004 JSON
- [Updated] Cisco ASA 113005 JSON
- [Updated] Cisco ASA 113012-17 JSON
- [Updated] Cisco ASA 209004 JSON
- [Updated] Cisco ASA 302020-1 JSON
- [Updated] Cisco ASA 303002 JSON
- [Updated] Cisco ASA 304001 JSON
- [Updated] Cisco ASA 304002 JSON
- [Updated] Cisco ASA 305011-12 JSON
- [Updated] Cisco ASA 313001 JSON
- [Updated] Cisco ASA 313004 JSON
- [Updated] Cisco ASA 313005 JSON
- [Updated] Cisco ASA 314003 JSON
- [Updated] Cisco ASA 322001 JSON
- [Updated] Cisco ASA 338001-8+338201-4 JSON
- [Updated] Cisco ASA 4000nn JSON
- [Updated] Cisco ASA 406001 JSON
- [Updated] Cisco ASA 406002 JSON
- [Updated] Cisco ASA 419001 JSON
- [Updated] Cisco ASA 419002 JSON
- [Updated] Cisco ASA 500004 JSON
- [Updated] Cisco ASA 602303-4 JSON
- [Updated] Cisco ASA 605004-5 JSON
- [Updated] Cisco ASA 710002-3 JSON
- [Updated] Cisco ASA 710005 JSON
- [Updated] Cisco ASA tcp_udp_sctp_teardowns JSON
Parsers
- [Updated] /Parsers/System/VMware/Carbon Black Cloud
- [Updated] /Parsers/System/Cisco/Cisco ASA
July 8, 2022 - Application Update
Announcement
- The built-in HipChat Action will be deprecated on August 25, 2022.
Minor Changes and Enhancements
- [Updated] An option has been added to the Enrichments tab which allows the user to hide any empty fields in the results.
Resolved Issues
- In some cases, changes to Rule Tuning Expressions were not being written to the Audit Logs properly.
- Mapper field format_parameters was not populating.
- Some of the links on the Related Entities tab of the Insight detail pages were malformed.
July 8, 2022 - Application Update
Announcement
The built-in HipChat Action will be deprecated on August 25, 2022.
Minor Changes and Enhancements
- [Updated] An option has been added to the Enrichments tab which allows the user to hide any empty fields in the results.
Resolved Issues
In some cases, changes to Rule Tuning Expressions were not being written to the Audit Logs properly.
tags: application
July 7, 2022 - Content Release
Rules
- [New] MATCH-S00816 Interactive Logon to Domain Controller
Log Mappers
- [Updated] Palo Alto GlobalProtect - Custom Parser
- Updated] Palo Alto GlobalProtect Auth - Custom Parser
- [Updated] Windows - System - 7045
- [Updated] Zscaler - Nanolog Streaming Service - JSON
Parsers
- [Updated] /Parsers/System/F5/F5 Syslog
- [Updated] /Parsers/System/Google/GCP
- [Updated] MATCH-S00246 AWS CloudTrail - GetSecretValue from non Amazon IP
- [Updated] THRESHOLD-S00096 Brute Force Attempt
- [Updated] MATCH-S00565 Direct Outbound DNS Traffic
- [Updated] THRESHOLD-S00103 Domain Brute Force Attempt
- [Updated] THRESHOLD-S00102 Domain Password Attack
- [Updated] THRESHOLD-S00099 Long URL Containing SQL Commands
- [Updated] THRESHOLD-S00095 Password Attack
- [Updated] CHAIN-S00008 Successful Brute Force
- [Updated] MATCH-S00185 Windows - Remote System Discovery
July 5, 2022 - Content Release
Rules
- [Updated] MATCH-S00246 AWS CloudTrail - GetSecretValue from non Amazon IP
- [Updated] THRESHOLD-S00096 Brute Force Attempt
- [Updated] MATCH-S00565 Direct Outbound DNS Traffic
- [Updated] THRESHOLD-S00103 Domain Brute Force Attempt
- [Updated] THRESHOLD-S00102 Domain Password Attack
- [Updated] THRESHOLD-S00099 Long URL Containing SQL Commands
- [Updated] THRESHOLD-S00095 Password Attack
- [Updated] CHAIN-S00008 Successful Brute Force
- [Updated] MATCH-S00185 Windows - Remote System Discovery
Log Mappers
- [Updated] McAfee Endpoint Security Custom Parser
- [Updated] Microsoft SQL Server Parser - Authentication
Parsers
- [Updated] /Parsers/System/Linux/Linux OS Syslog
- [Updated] /Parsers/System/McAfee/McAfee EPO XML
- [Updated] /Parsers/System/Microsoft/Microsoft SQL Server
- [Updated] /Parsers/System/Palo Alto/PAN Firewall CSV
- [Updated] /Parsers/System/Twistlock/Twistlock
In the Cloud SIEM Enterprise release notes, you'll find information about new and enhanced features, updated content (like rules, log mappers and parsers), bug fixes, and other important announcements.
To view release notes from previous years, check the archive.
RSS Feed