CyberArk EPM Source

The CyberArk Endpoint Privilege Manager (EPM) is a security solution that helps organizations reduce the risk of information theft or ransomware attacks by enforcing the principle of least privilege and preventing unauthorized access to critical systems and data. The solution employs a combination of privilege security, application control, and credential theft prevention to reduce the likelihood of malware infections.
The integration with CyberArk EPM's API allows for retrieving administrative, detailed raw, and policy audit events from every set in the environment. The API documentation provides guidance on accessing and utilizing this information. This integration facilitates retrieving various audit events, including administrative actions, policy violations, and application usage, to generate alerts, reports, and remediation actions that enhance the organization's security posture.
Data Sources
The CyberArk EPM ingests sets, admin audit events, detailed raw events, and aggregated policy audit events from the CyberArk API and sends data to Sumo Logic.
- Sets. CyberArk EPM organizes systems into logical groups based on shared attributes such as operating system type or location.
- Admin Audit Events. CyberArk EPM captures events generated by users performing actions via the EPM console or remotely through API after logging in.
- Detailed Raw Events. CyberArk EPM gathers detailed raw events from endpoints and other sources in the environment.
- Aggregated Policy Audit Events. CyberArk EPM logs events created by policies enforced on applications running on endpoint computers.
These components enable organizations to effectively monitor and manage endpoint security, identify potential risks and vulnerabilities, and take proactive measures to safeguard their critical assets. By leveraging insights from these events, organizations can enhance their overall security posture and better protect against cyber threats.
Metadata Fields
Metadata fields will be set, if the integration is configured with the SIEM forward option. See Metadata Fields table below:
| Fields | Value |
|---|---|
_siemVendor | Cyber-Ark |
_siemProduct | EPM |
_siemFormat | JSON |
_parser | /Parsers/System/Cyber-Ark/CyberArk EPM JSON |
States
An CyberArk Source lets you pull audit logs from the CyberArk APIs. When you create an CyberArk C2C Source, it goes through the following states:
- Pending. Once the Source is submitted, it is validated, stored, and placed in a Pending state.
- Started. A collection task is created on the Hosted Collector.
- Initialized. The task configuration is complete in Sumo Logic.
- Authenticated. The Source is successfully authenticated with the CyberArk APIs.
- Collecting. The Source is actively collecting data from the CyberArk APIs.
If the Source has any issues during any one of these states, it is placed in an Error state.
When you delete the Source, it is placed in a Stopping state. When it has successfully stopped, it is deleted from your Hosted Collector. On the Collection page, the Health and Status for Sources is displayed. Use Health Events to investigate issues with collection.
Hover your mouse over the status icon to view a tooltip with a count of the detected errors and warnings. You can click on the status icon to open a Health Events panel with details on each detected issue.
Setup and Configuration
In this configuration, you will set up a CyberArk EPM source account and configure it to be authorized and authenticated to use CyberArk API. CyberArk EPM supports EPM Authentication. It authenticates a user to EPM using the username and password and returns a token and EPM server URL. To set up a CyberArk account, follow the steps below:
- Navigate to CyberArk application.
- Enter the Username and Password of your choice. You can enter any combination of letters, numbers, or special characters for both the username and password. There are no limitations on the length or complexity of the username and password either.

Create a CyberArk EPM Source
When you create a CyberArk EPM Source, you add it to a Hosted Collector. Before creating the Source, identify the Hosted Collector you want to use or create a new Hosted Collector. For instructions, see Configure a Hosted Collector.
To configure a CyberArk EPM Source, follow the steps below:
- In Sumo Logic, select Manage Data > Collection > Collection.
- On the Collectors page, click Add Source next to a Hosted Collector.
- Select CyberArk EPM.

- Name. Enter a name to display for the Source in the Sumo Logic web application.
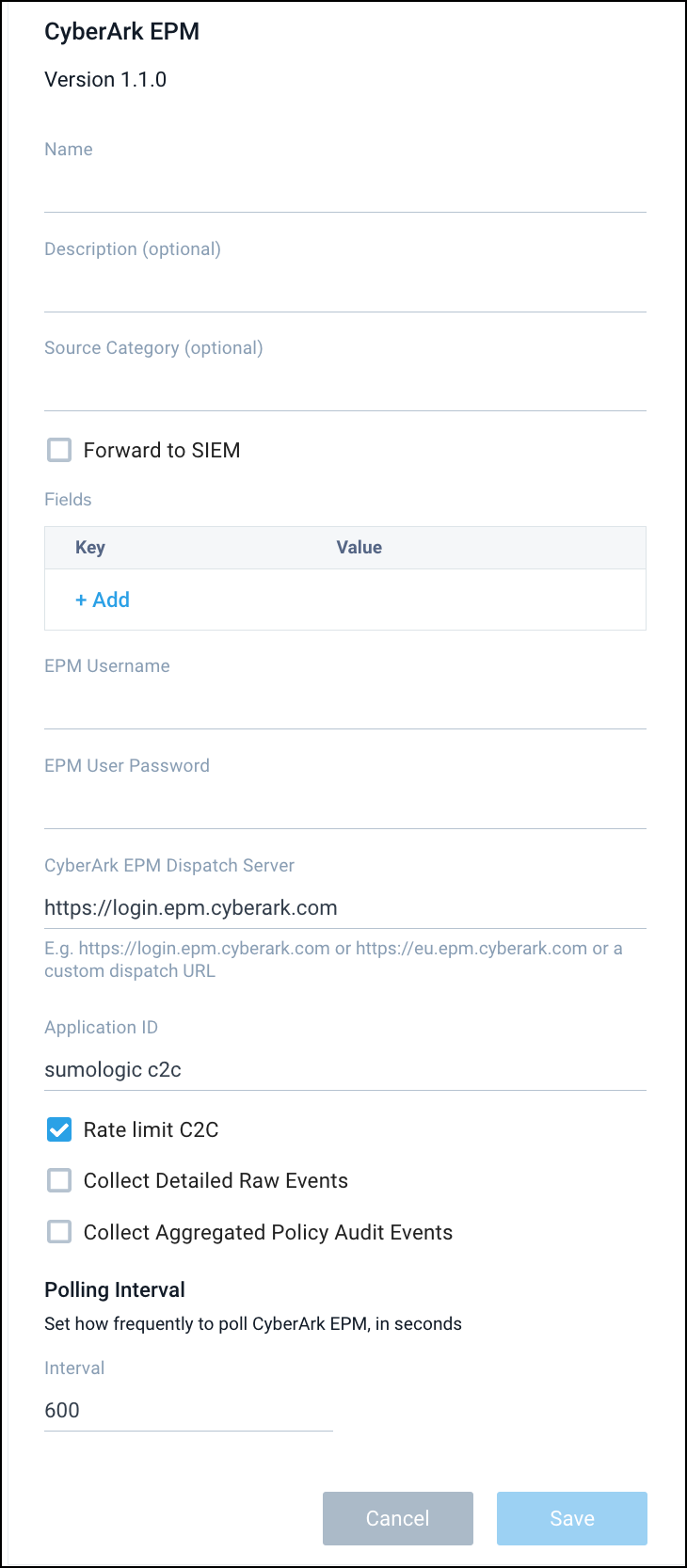
- Description. (Optional)
- Source Category. Enter any string to tag the output collected from the Source. Category metadata is stored in a searchable field called
_sourceCategory. - Forward to SIEM. Check the checkbox to forward your data to Cloud SIEM Enterprise. When configured with the Forward to SIEM option the following metadata fields are set:
_siemVendor—Cyber-Ark_siemProduct—EPM_siemFormat—JSON_parser—/Parsers/System/Cyber-Ark/CyberArk EPM JSON
- Fields. (Optional) Click +Add to ad additional fields; each field needs a name (key) and value.
A green circle with a check mark is shown when the field exists and is enabled in the Fields table schema.
An orange triangle with an exclamation point is shown when the field doesn't exist, or is disabled, in the Fields table schema. In this case, an option to automatically add or enable the nonexistent fields to the Fields table schema is provided. If a field is sent to Sumo that does not exist in the Fields schema or is disabled it is ignored, known as dropped.
- EPM Username. Enter your EPM username from the Setup and Configuration section.
- EPM User Password. Enter your EPM password from the Setup and Configuration section.
- CyberArk EPM Dispatch Server. Enter your CyberArk EPM Dispatch Server URL, it is the dispatch server for your region. Following are some examples of dispatch server URLs:
- For the US datacenter, the dispatch server URL is
https://login.epm.cyberark.com. - For the EU datacenter, the dispatch server URL is
https://eu.epm.cyberark.com.
- For the US datacenter, the dispatch server URL is
- Application ID. An application ID is a unique identifier that helps an API recognize which application or program is accessing it. It's like a name tag that allows the API to keep track of different applications using it. For example, sumologic.
- Rate Limit C2C. This option removes the request limitations imposed on the CyberArk C2C source, allowing it to make as many requests as possible. By default, the request limitations are set to 5 requests per minute for admin audit events and 1000 requests per 5 minutes for detailed raw and aggregated policy audit events. If you need to make more requests than the default limits allow, you can contact the CyberArk support team to request the limitations be removed.
- Collect detailed raw events. This option enables the CyberArk C2C Source to collect detailed raw events from the CyberArk EPM (Endpoint Privilege Manager).
- Collect aggregated policy audit events. This option enables the C2C Source to collect aggregated policy audit events from the CyberArk EPM (Endpoint Privilege Manager).
- Polling Interval. The polling interval is the frequency at which the CyberArk C2C Source will check for updates from the CyberArk EPM (Endpoint Privilege Manager). This field is pre-filled with 600.
- When you are finished configuring the Source, click Save.
Error Types
When Sumo Logic detects an issue it is tracked by Health Events. The following table shows the three possible error types, the reason the error would occur, if the Source attempts to retry, and the name of the event log in the Health Event Index.
| Type | Reason | Retries | Retry Behavior | Health Event Name |
|---|---|---|---|---|
| ThirdPartyConfig | Normally due to an invalid configuration. You'll need to review your Source configuration and make an update. | No retries are attempted until the Source is updated. | Not applicable | ThirdPartyConfigError |
| ThirdPartyGeneric | Normally due to an error communicating with the third party service APIs. | Yes | The Source will retry indefinitely. | ThirdPartyGenericError |
| FirstPartyGeneric | Normally due to an error communicating with the internal Sumo Logic APIs. | Yes | The Source will retry indefinitely. | FirstPartyGenericError |
JSON configuration
Sources can be configured using UTF-8 encoded JSON files with the Collector Management API. See how to use JSON to configure Sources for details.
| Parameter | Type | Required | Description | Access |
|---|---|---|---|---|
config | JSON Object | Yes | Contains the configuration-parameters of the Source. | |
schemaRef | JSON Object | Yes | Use {"type":"CyberArk EPM"} for CyberArk EPM Source. | not modifiable |
sourceType | String | Yes | Use Universal for CyberArk EPM Source. | not modifiable |
Config Parameters
| Parameter | Type | Required | Description | Access |
|---|---|---|---|---|
name | String | Yes | Type the desired name of the Source and it must be unique per Collector. This value is assigned to the metadata field _source. | modifiable |
description | String | No | Type the description of the Source. | modifiable |
category | String | No | Type the category of the source. This value is assigned to the metadata field _sourceCategory. | modifiable |
fields | JSON Object | No | JSON map of key-value fields (metadata) to apply to the Collector or Source. Use the boolean field _siemForward to enable forwarding to SIEM. | modifiable |
username | String | Yes | Username for your CyberArk EPM account. | modifiable |
password | String | Yes | Password for your CyberArk EPM account. | modifiable |
epm_server | String | Yes | Dispatch Server of the CyberArk EPM. | modifiable |
application_id | String | Yes | Unique identifier of the application who is accessing the API. | modifiable |
ratelimit | boolean | No | Removes the request limitations imposed on the CyberArk C2C source. | modifiable |
raw_events | boolean | No | Collects detailed raw events. | modifiable |
policy_audits | boolean | No | Collects aggregated policy audits events. | modifiable |
polling_interval | integer | Yes | Frequency of C2C updates from EPM. | modifiable |
CyberArk Source JSON example:
{
"api.version": "v1",
"source": {
"config": {
"name": "CyberArk Test",
"username": "user@sumologic.com",
"password": "Sumo@123",
"application_id": "sumologic-c2c",
"epm_server": "https://in.epm.cyberark.com",
"ratelimit": true,
"detailed_raw_events": false,
"aggregated_policy_audits": false,
"polling_interval": 30
},
"schemaRef": {
"type": "CyberArk EPM"
},
"sourceType": "Universal"
}
}
API Limitations
Session Timeout. The session timeout for all APIs is part of the session token and is defined by the Timeout for inactive session Server Configuration parameter.
Remove Request Limitations. It's important to note that the CyberArk C2C Source enforces limitations on the number of requests that can be made to the server by default. In addition, the server may have its own limit on how many calls can be made within a minute. For more information, refer to the API Limitations documentation.
When setting the poll frequency, it's recommended to consider these limitations and set the frequency to a reasonable value to ensure that the C2C operates efficiently without overwhelming the server.