Collect Amazon CloudWatch Logs using a CloudFormation Template with Secured Sumo Endpoint
The below steps assumes you have configured a Hosted collector and an HTTP Source as specified in this section.
Download the CloudFormation template
Sumo Logic provides a CloudFormation template to make setup easier. If you want to make any of the optional modifications described in this section, download the DLQLambdaCloudFormationWithSecuredEndpoint.json CloudFormation template from https://s3.amazonaws.com/appdev-cloudformation-templates/DLQLambdaCloudFormationWithSecuredEndpoint.json and make modifications. Otherwise, proceed to Create a SecureString Parameter console.
Create a SecureString Parameter
You can create the parameter via AWS CLI or via Console.
If you're using AWS CLI use the below command:
aws ssm put-parameter --region us-east-1 --cli-input-json '{
"Name": "SUMO_ENDPOINT",
"Value": \<Paste the endpoint of the HTTP source created in step >",
"Type": "SecureString"
}'
The above command uses the default AWS Managed Key. If you want to use Customer Managed CMK, refer Create a SecureString parameter using a customer managed CMK.
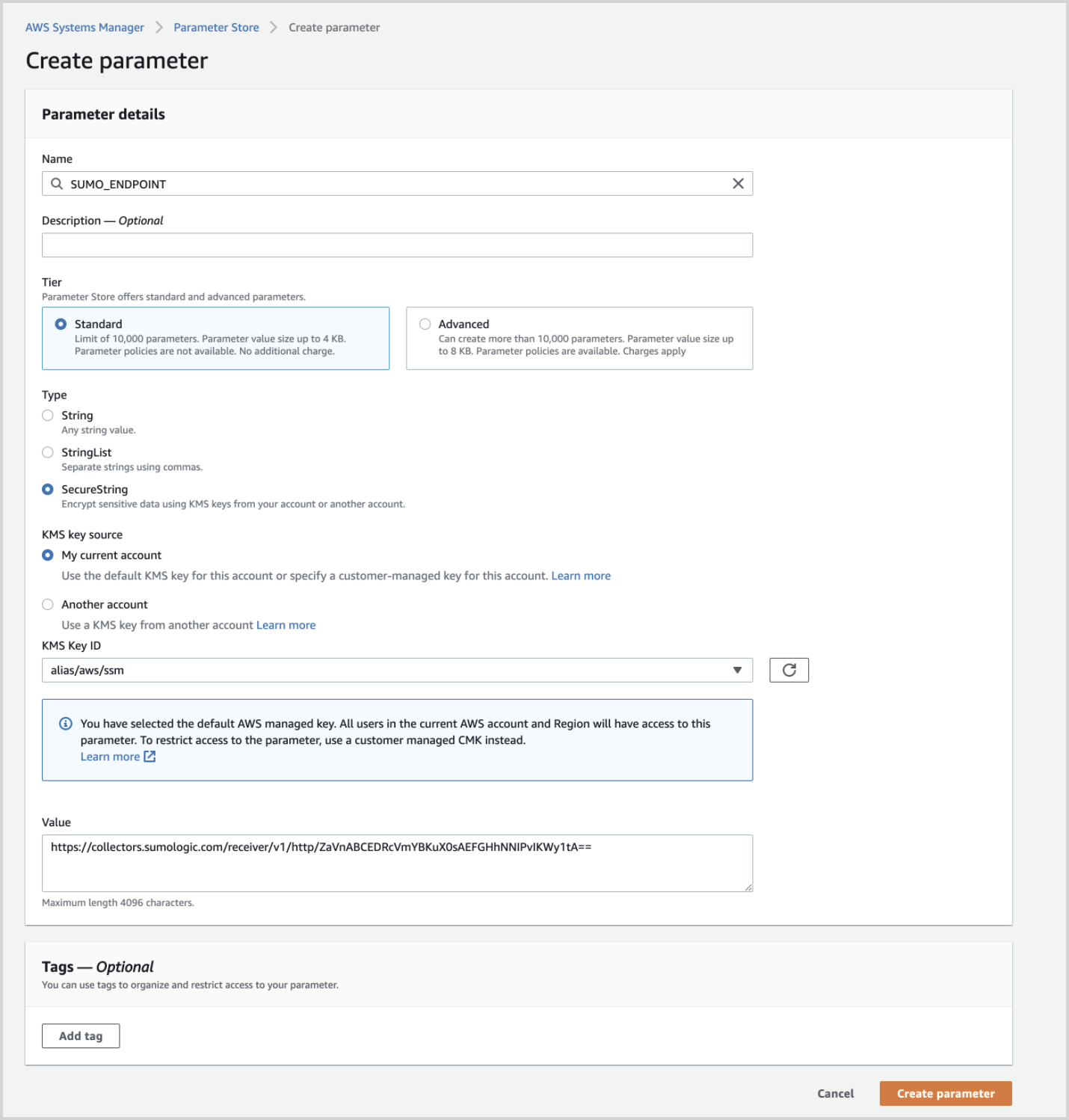
If you're using AWS Console do the following:
Go to https://console.aws.amazon.com/systems-manager/parameters.
- Name. SUMO_ENDPOINT
- Tier. Standard
- Type. Select SecureString
- KMS Key Source. Select the KMS Key ID or you can use the default KMS key.
- Value. Paste the value of the SUMO_ENDPOINT_URL copied while creating the HTTP source.
Click Save Parameter.
You can verify whether the parameter is created successfully by going to https://console.aws.amazon.com/systems-manager/parameters/?region=us-east-1&tab=Table and looking for parameter SUMO_ENDPOINT.
Get the KMS Key ID
Follow the steps in this document to get the Key ID used to encrypt/decrypt the parameter created earlier. If you're using default AWS Managed Key the Key ID should be corresponding to the alias value aws/ssm.
Create a stack on the AWS CloudFormation console
Log in to the AWS Management Console.
Under Management Tools, select CloudFormation.
Create a new stack by clicking Create Stack, then select “With new resources (standard).”
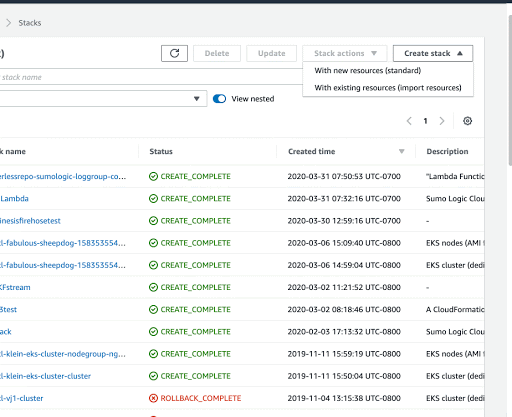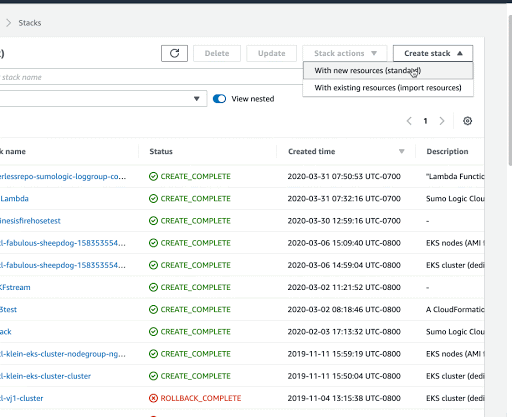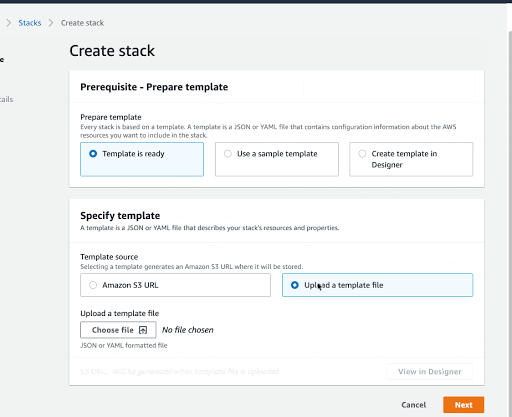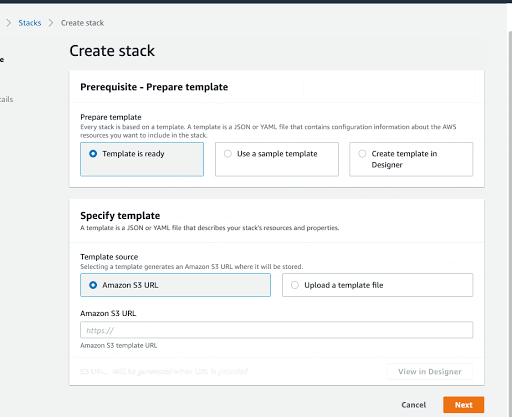
On the Specify Template window, do one of the following:
If you have downloaded and optionally modified the CloudFormation template, choose to Upload a template file, upload the
DLQLambdaCloudFormationWithSecuredEndpoint.jsonfile, and then click Next.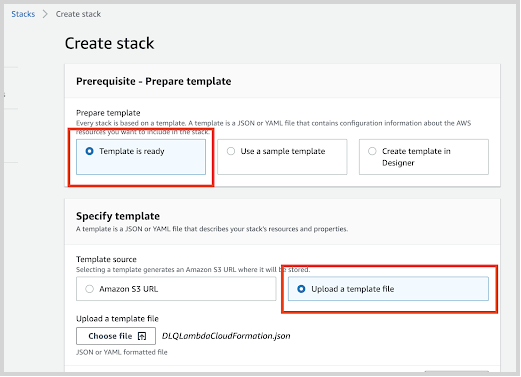
Otherwise, if you did not modify the CloudFormation template, select Specify an Amazon S3 template URL and enter:
https://s3.amazonaws.com/appdev-cloudformation-templates/DLQLambdaCloudFormationWithSecuredEndpoint.json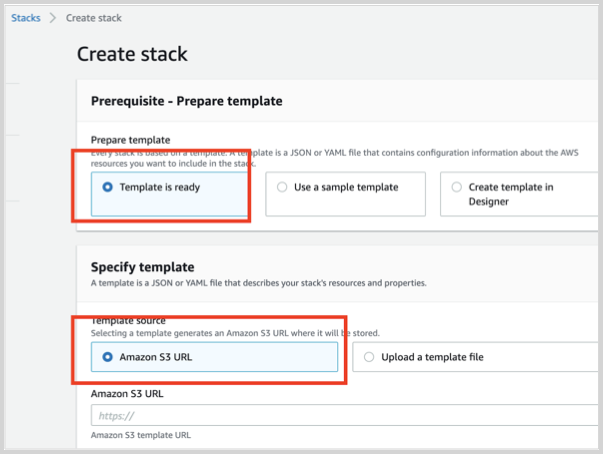
Select Next and the Specify Stack Details window appears. Enter the following:
Stack Name.
EmailID (Optional). Used for alerts.
IncludeLogGroupInfo. Set to true to include loggroup/logstream values in logs. The default value is False. For AWS Lambda Logs IncludeLogGroupInfo must be set to True; for VPC Flow Logs it's optional.
LogFormat. For VPC logs, choose either VPC-JSON (JSON format) or VPC-RAW (raw messages). The default value is Others.
LogStreamPrefix (Optional). Enter a comma-separated list of logStream name prefixes to filter by logStream. Please note this is separate from a logGroup. This is used to only send certain logStreams within a CloudWatch logGroup(s). LogGroup(s) still need to be subscribed to the created Lambda function (
SumoCWLogsLambda-<Auto-Genereted-Suffix>), regardless of what is input for this value.noteLogStreamPrefix field does not accept special characters (
[|\{}()[\]^$+*?.-]). For example, you can use the comma-separated list like test-name, test-logs as the LogStream name prefixes.NumOfWorkers. (Optional) Increase this value to speed up the dead letter queue (DLQ) processing.
SumoURLDecryptKeyID. (Required) Enter the Key ID copied from “Get the KMS Key ID” step.
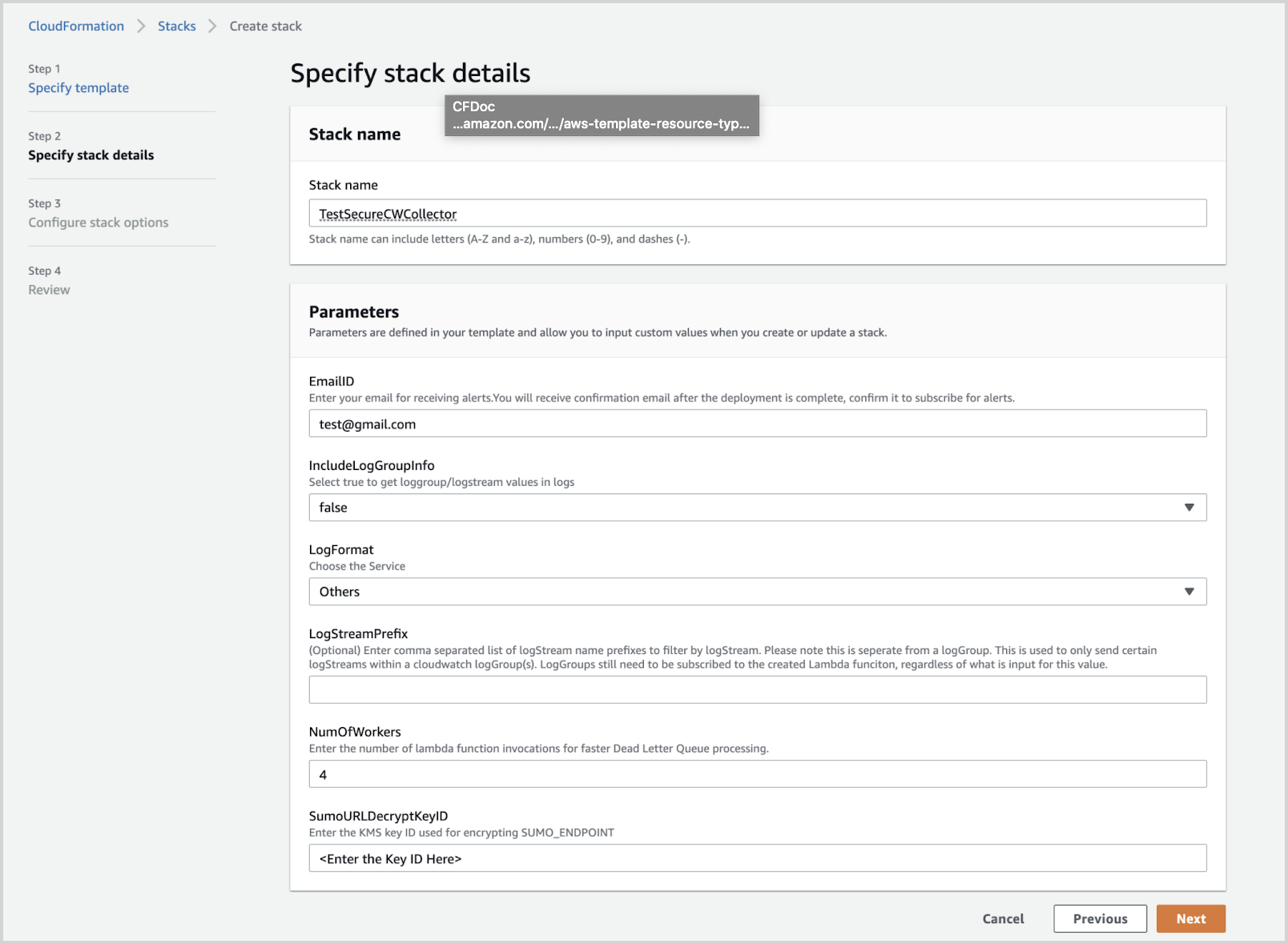
Click Next. The Configure Stack Options screen will appear. You can optionally add AWS tags to tag the resources created by this Cloudformation stack. Click Next to get to the final Review window.
In the Review window, click the checkbox acknowledging that you understand the template creates IAM resources, and click Create.
After a few minutes, you will see CREATE_COMPLETE in the Status column.
If you're using an existing log group or if you don’t want to send logs to the default group SumoCWLogGroup then you must do one of the following: Manually subscribe the SumoCWLogsLambda to an existing CloudWatch Log Group, create a subscription filter manually, or Auto-Subscribe AWS Log Groups to a Lambda Function.
Now go back to the section and follow the instructions for remaining steps.